“The Weather Channel is an American basic cable and satellite television channel which broadcasts weather forecasts and weather-related news and analyses, along with documentaries and entertainment programming related to weather. Launched on May 2, 1982, the channel broadcasts weather forecasts and weather-related news and analysis, along with documentaries and entertainment programming related to weather.”
“As of February 2015, The Weather Channel was received by approximately 97.3 million American households that subscribe to a pay television service (83.6% of U.S. households with at least one television set), which gave it the highest national distribution of any U.S. cable channel. However, it was subsequently dropped by Verizon FiOS (losing its approximately 5.5 millions subscribers), giving the title of most distributed network to HLN. Actual viewership of the channel averaged 210,000 during 2013 and has been declining for several years. Content from The Weather Channel is available for purchase from the NBCUniversal Archives.” (Wikipedia)
Vulnerability description:
The Weather Channel has a cyber security problem. Hacker can exploit it by XSS bugs.
Almost all links under the domain weather.com are vulnerable to XSS attacks. Attackers just need to add script at the end of The Weather Channel’s URLs. Then the scripts will be executed.
10 thousands of Links were tested based a self-written tool. During the tests, 76.3% of links belong to weather.com were vulnerable to XSS attacks.
The reason of this vulnerability is that Weather Channel uses URLs to construct its HTML tags without filtering malicious script codes.
The vulnerability can be attacked without user login. Tests were performed on Firefox (34.0) in Ubuntu (14.04) and IE (9.0.15) in Windows 8.
POC Codes, e.g.
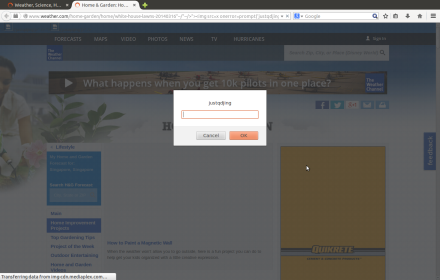
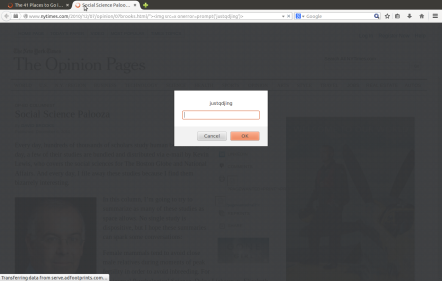
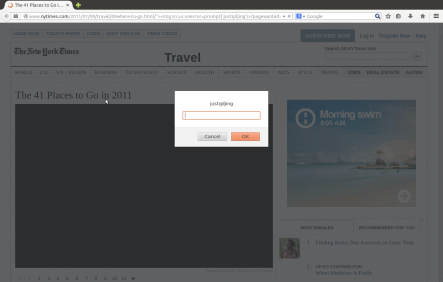
http://www.weather.com/slideshows/main/“–/>”><img src=x onerror=prompt(‘justqdjing’)>
http://www.weather.com/home-garden/home/white-house-lawns-20140316%22–/“–/>”><img src=x onerror=prompt(‘justqdjing’)>t%28%27justqdjing%27%29%3E
http://www.weather.com/news/main/“><img src=x onerror=prompt(‘justqdjing’)>
The Weather Channel has patched this Vulnerability in late November, 2014 (last Week). “The Full Disclosure mailing list is a public forum for detailed discussion of vulnerabilities and exploitation techniques, as well as tools, papers, news, and events of interest to the community. FD differs from other security lists in its open nature and support for researchers’ right to decide how to disclose their own discovered bugs. The full disclosure movement has been credited with forcing vendors to better secure their products and to publicly acknowledge and fix flaws rather than hide them. Vendor legal intimidation and censorship attempts are not tolerated here!” A great many of the fllowing web securities have been published here, Buffer overflow, HTTP Response Splitting (CRLF), CMD Injection, SQL injection, Phishing, Cross-site scripting, CSRF, Cyber-attack, Unvalidated Redirects and Forwards, Information Leakage, Denial of Service, File Inclusion, Weak Encryption, Privilege Escalation, Directory Traversal, HTML Injection, Spam. This bug was published at The Full Disclosure in November, 2014.
More Details:
http://seclists.org/fulldisclosure/2014/Nov/89
http://lists.openwall.net/full-disclosure/2014/11/27/3
http://permalink.gmane.org/gmane.comp.security.fulldisclosure/1253
https://progressive-comp.com/?l=full-disclosure&m=141705578527909&w=1
http://whitehatview.tumblr.com/post/104313615841/the-weather-channel-flaw
http://www.inzeed.com/kaleidoscope/xss-vulnerability/the-weather-channel-exploit
http://diebiyi.com/articles/security/the-weather-channel-bug
http://whitehatpost.lofter.com/post/1cc773c8_6f2d4a8
https://vulnerabilitypost.wordpress.com/2014/12/04/the-weather-channel-flaw
http://tetraph.blog.163.com/blog/static/234603051201411475314523/
http://tetraph.blogspot.com/2014/12/the-weather-channel-xss.html
http://ithut.tumblr.com/post/121916595448/weather-channel-xss
https://mathfas.wordpress.com/2014/12/04/the-weather-channel-weather-bug
http://computerobsess.blogspot.com/2014/12/the-weather-channel-xss.html
http://www.tetraph.com/blog/xss-vulnerability/the-weather-channel-bug